Enumeration in Post-Exploitation: Expanding Access on Compromised Systems
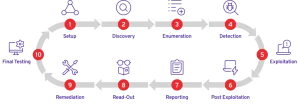
In the realm of cybersecurity, post-exploitation is a crucial phase for attackers seeking to maintain access and control over compromised systems. Enumeration, a key component of post-exploitation, plays a significant role in this process. It involves gathering detailed information about the target system, such as user accounts, network resources, and security configurations. In this article, we will delve into the concept of enumeration in post-exploitation and explore its various techniques, highlighting its importance, risks, and preventive measures.
1.Understanding Enumeration in Post-Exploitation
Enumeration, in the context of cybersecurity, is the systematic process of extracting valuable information from a compromised system. Once an attacker gains unauthorized access to a target, they proceed with enumeration to escalate privileges, identify potential vulnerabilities, and map out the network’s structure. The goal is to extend control over the system and, if possible, move laterally to other connected systems within the network.
2.Techniques Used in Enumeration
3.Service and Port Scanning
Service and port scanning is one of the fundamental techniques in enumeration. It involves scanning the target system for open ports and the services running on those ports. This information helps attackers identify potential entry points and vulnerabilities that could be exploited to gain further access.
-
User Account Enumeration
User account enumeration is the process of identifying valid user accounts on the compromised system. Attackers attempt to discover existing accounts, including privileged ones, to understand the user hierarchy and gain access to sensitive data.
-
Network Resource Enumeration
Network resource enumeration involves identifying shared resources, such as file shares, printers, and directories, on the compromised system. Accessing these resources can provide attackers with valuable data and lateral movement opportunities.
-
Enumeration of Installed Software
Attackers often enumerate the software installed on the compromised system to locate outdated or vulnerable applications. Exploiting these vulnerabilities can lead to complete control over the system.
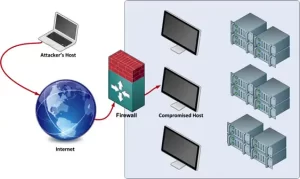
4.The Importance of Enumeration in Post-Exploitation
Enumeration plays a critical role in the success of a post-exploitation attack. By meticulously gathering information about the compromised system and its network, attackers can:
-
Maintain Persistence:
Enumeration helps attackers identify backdoors or hidden access points, allowing them to maintain control over the system even after remediation attempts.
-
Privilege Escalation:
Discovering user accounts with elevated privileges enables attackers to escalate their own privileges and gain access to more sensitive areas of the system.
-
Lateral Movement:
Knowledge of network resources aids in moving laterally across the network, potentially compromising other interconnected systems.
-
Data Exfiltration:
Enumeration may reveal valuable data, such as intellectual property or customer information, which attackers can exfiltrate for malicious purposes.
Risks Associated with Enumeration
While enumeration is a powerful tool for attackers, it also comes with inherent risks:
-
Detection:
Excessive or careless enumeration attempts may trigger security alerts, leading to faster detection and response from defenders.
-
Disruption:
In some cases, aggressive enumeration techniques could disrupt the target system or network, drawing unwanted attention.
-
Legal Consequences:
Engaging in unauthorized enumeration is illegal and may result in severe legal repercussions for attackers.
5.Preventive Measures
Defenders can implement several preventive measures to mitigate the risk of successful enumeration:
-
Firewalls and Intrusion Detection Systems (IDS):
Properly configured firewalls and IDS can detect and block excessive enumeration attempts.
-
Access Controls:
Enforcing strict access controls and permissions can limit an attacker’s ability to escalate privileges.
-
Regular System Patching:
Keeping systems and software up-to-date helps minimize vulnerabilities that attackers could exploit.
-
Monitoring and Logging:
Continuous monitoring and comprehensive logging can aid in the early detection of suspicious activities.
6. Best Practices for Effective Enumeration
To conduct effective enumeration during post-exploitation, attackers should adhere to certain best practices:
-
Stealth and Patience:
Attackers must employ stealthy techniques to avoid detection during enumeration. Rushing the process may raise suspicion and lead to defensive actions.
-
Limited Queries:
Restricting the number of queries during enumeration can reduce the risk of triggering security mechanisms designed to detect suspicious activities.
-
Use of Encrypted Channels:
Encrypting communication channels between the attacker and the compromised system can help evade network monitoring tools.
-
Avoid Anomalous Behavior:
Attackers should mimic normal user behavior during enumeration to blend in with regular network traffic.
-
Regularly Update Techniques:
As defenders enhance their security measures, attackers must stay up-to-date with the latest enumeration techniques to overcome new challenges.
7. Case Study: Enumeration Gone Wrong
In a real-world scenario, a company fell victim to a cyber attack due to flawed enumeration practices. The attackers, eager to expand their access, conducted extensive port scanning and aggressive user account enumeration, leading to an increased network load. The abnormal activity triggered the company’s intrusion detection system, alerting their security team. Prompt investigation revealed the ongoing attack, and the security team swiftly neutralized the threat, preventing any data breach or further damage.
This case study highlights the significance of using cautious and measured enumeration techniques to avoid detection and improve the chances of maintaining access.
8. Ethical Enumeration
Enumeration is a double-edged sword that can be used for both malicious and ethical purposes. Ethical enumeration involves authorized security professionals conducting enumeration to identify weaknesses and vulnerabilities within their organization’s systems. The goal is to proactively strengthen security measures and safeguard against potential cyber attacks.
Security teams often engage in ethical enumeration through penetration testing and vulnerability assessments. This proactive approach helps organizations identify and patch vulnerabilities before malicious actors can exploit them.
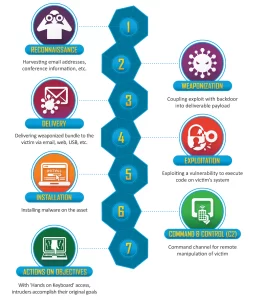
Conclusion
Enumeration in post-exploitation is an essential aspect of a cyber attacker’s arsenal, allowing them to gather crucial information and expand their control over compromised systems. However, this process comes with significant risks and legal consequences. Organizations must prioritize cybersecurity by implementing preventive measures and staying vigilant against potential threats.
For ethical cybersecurity professionals, enumeration serves as a valuable tool to identify and address weaknesses within an organization’s infrastructure. Conducting enumeration responsibly can help fortify defenses and ensure the security and privacy of sensitive data.
In the dynamic and ever-evolving world of cybersecurity, understanding the intricacies of enumeration and its implications empowers defenders to stay one step ahead of potential adversaries. Through constant vigilance, proactive measures, and adherence to best practices, organizations can strengthen their cybersecurity posture and protect their valuable assets from the ever-present threats of the digital landscape.
