Introduction
Choosing the right tools is crucial for any organization’s cybersecurity framework. Evaluating and testing tools before making a decision ensures they meet specific requirements and integrate seamlessly into existing systems.
This article provides actionable insights on evaluating and testing tools, with a focus on emerging trends in SIEM (Security Information and Event Management) technology. Whether you’re a business owner or IT professional, these tips will help you make informed decisions.
Understanding the Importance of Tool Evaluation and Testing
Why Testing Tools Matters in Cybersecurity
In cybersecurity, the stakes are high. Tools must function as intended to detect threats and mitigate risks.
Testing allows organizations to:
- Identify potential shortcomings.
- Verify compatibility with existing systems.
- Ensure compliance with industry regulations.
Proper evaluation builds confidence in tool performance and avoids costly mistakes.
Key Factors to Consider When Evaluating Tools
Usability and User Experience
Usability directly impacts how effectively a tool is adopted within an organization. Key considerations include:
- Intuitive interfaces.
- Customizable dashboards.
- Accessibility for all users.
A user-friendly tool saves time and reduces the likelihood of errors.
Integration and Compatibility
No tool operates in isolation. Evaluate:
- Compatibility with current infrastructure.
- API support for seamless integration.
- Vendor support for future updates.
Tools that integrate well enhance productivity and minimize disruptions.
Best Practices for Testing Software Tools
Testing for Real-World Scenarios
Simulating real-world conditions is critical. This involves:
- Stress testing to measure tool resilience.
- Role-based testing to evaluate performance under different user profiles.
- Testing in a controlled environment before deployment.
These practices help predict how a tool will perform in critical situations.
Benchmarking Against Industry Standards
Comparing tools against industry benchmarks ensures they meet performance expectations. Key steps include:
- Reviewing performance metrics.
- Checking for compliance with cybersecurity standards like ISO/IEC 27001.
- Leveraging third-party audits and certifications.

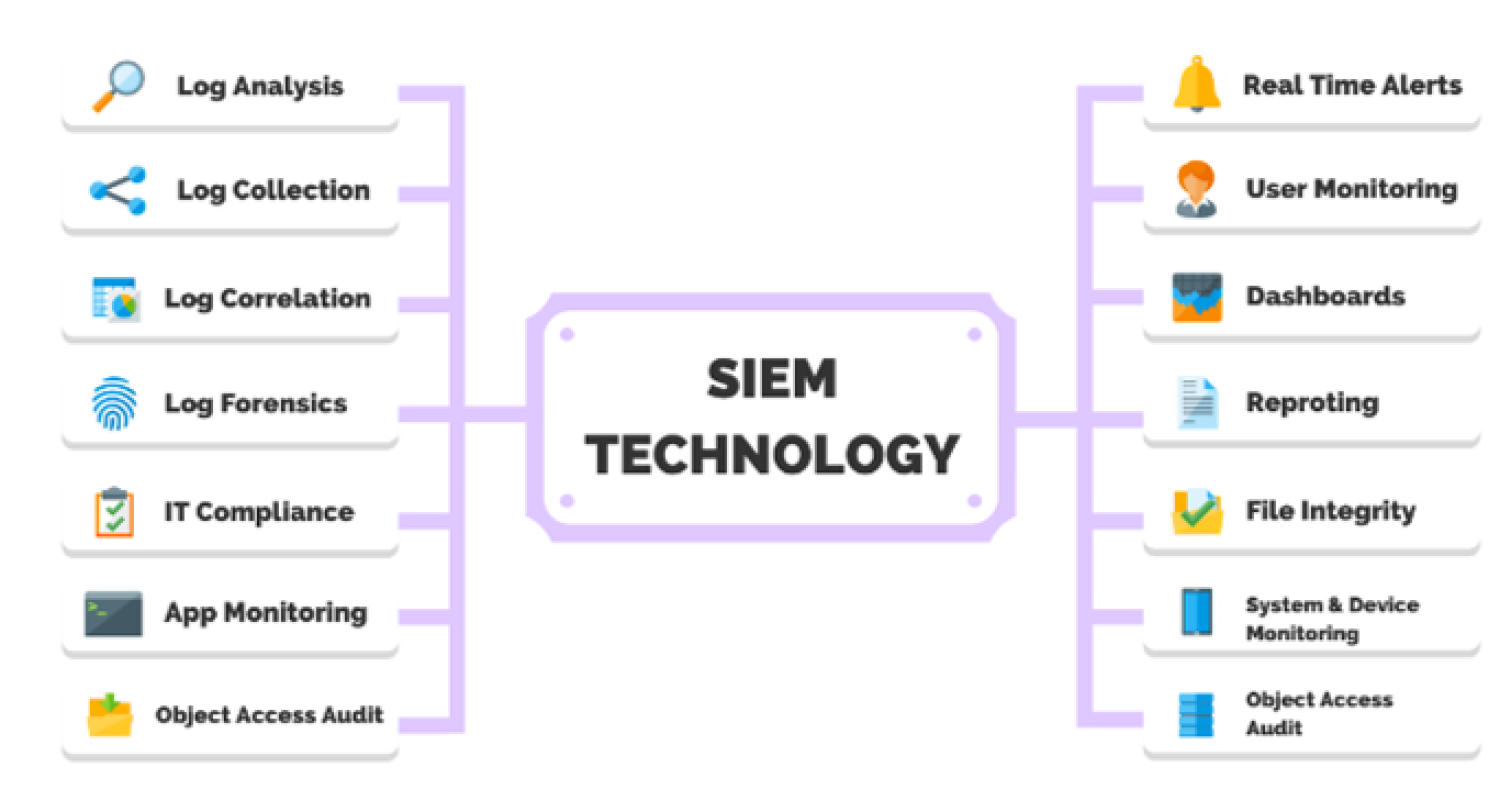
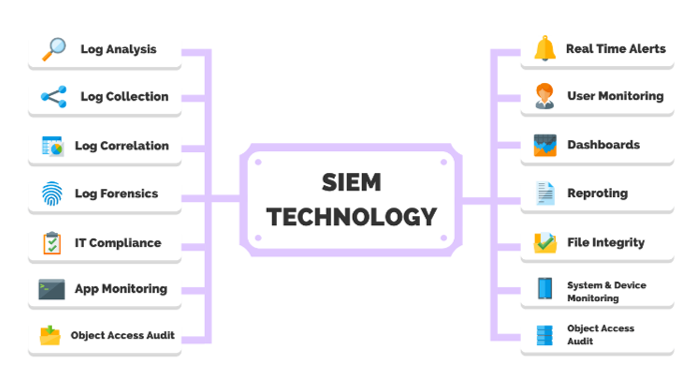
Emerging Trends in SIEM Technology
AI and Machine Learning in SIEM
Artificial intelligence and machine learning are revolutionizing SIEM technology. Benefits include:
- Automated threat detection.
- Reduced false positives through behavioral analysis.
- Enhanced incident response times.
These advancements improve efficiency and accuracy in identifying potential threats.
Cloud-Based SIEM Solutions
Cloud adoption is driving innovation in SIEM tools. Advantages include:
- Scalability for growing organizations.
- Cost-effectiveness through subscription models.
- Real-time data processing and reporting.
Cloud-based solutions are especially beneficial for remote and hybrid work environments.
User Behavior Analytics (UBA)
UBA leverages data to identify anomalies in user behavior. Key applications are:
- Detecting insider threats.
- Monitoring unusual login patterns.
- Enhancing overall security policies.
UBA adds an extra layer of intelligence to SIEM platforms.
Making the Final Decision
Cost vs. Value Analysis
When assessing costs, consider:
- Licensing fees.
- Maintenance and support costs.
- Long-term ROI based on tool efficiency.
Balancing cost with functionality ensures optimal resource allocation.
Feedback from Pilot Testing
Pilot testing provides invaluable insights. During this phase:
- Gather feedback from end-users.
- Identify potential challenges in implementation.
- Fine-tune configurations to meet organizational needs.
Incorporating feedback ensures the tool aligns with operational goals.
Conclusion
Evaluating and testing tools before committing to a decision is essential in today’s cybersecurity landscape. By considering usability, compatibility, and emerging trends like AI, cloud-based solutions, and UBA, organizations can enhance their security framework.
Making informed choices now can save time, money, and resources in the future.
Thanks & Regards
Ashwini Kamble