The Growing Security Challenges of IoT Devices

The Internet of Things (IoT) has transformed our lives in numerous ways, creating a more interconnected world where devices communicate seamlessly to enhance our daily experiences. From smart homes to industrial applications, the convenience and efficiency offered by IoT devices are undeniable. However, as this technology continues to proliferate, it brings with it a host […]
Google’s E-A-T How to Build Content That Ranks Higher

In the world of search engine optimization (SEO), Google’s E-A-T framework plays a pivotal role in determining how well your content ranks. E-A-T stands for Expertise, Authoritativeness, and Trustworthiness, and these factors are critical in how Google evaluates your content. To achieve higher search rankings, it’s essential to understand how to create content that adheres […]
Content Brief: Edge Computing vs. Cloud Computing: Which One Should You Choose?

Introduction With the rapid advancement in technology, businesses face the challenge of selecting the best infrastructure for managing data. Two prominent options stand out—Edge Computing and Cloud Computing. Both technologies offer unique advantages, but choosing the right one depends on several factors like latency, scalability, and cost. This blog post will break down the differences and help […]
AI in Everyday Life: Practical Applications You Didn’t Know About

Artificial Intelligence (AI) has rapidly evolved from a futuristic concept to an integral part of our daily lives. While many are familiar with AI through popular applications like virtual assistants and recommendation algorithms, its practical applications extend far beyond these common uses. This blog explores the myriad ways AI influences our everyday lives, highlighting tools […]
Ransomware Defense: Proven Strategies to Protect Your Business
In today’s digital landscape, ransomware attacks have become increasingly prevalent and sophisticated, targeting businesses of all sizes. These malicious attacks can cripple organizations, resulting in data loss, financial strain, and reputational damage. As a business leader, understanding how to effectively defend against ransomware is paramount. This blog outlines proven strategies that can help protect your […]
Best Practices for Securing Your Cloud Infrastructure

In today’s digital landscape, cloud computing has transformed the way businesses operate. While the cloud offers numerous advantages, such as scalability, cost savings, and flexibility, it also introduces new security challenges. Securing your cloud infrastructure is paramount to protect sensitive data and maintain compliance. In this blog, we’ll explore best practices for cloud security, focusing […]
DevOps Best Practices to Streamline Your IT Operations
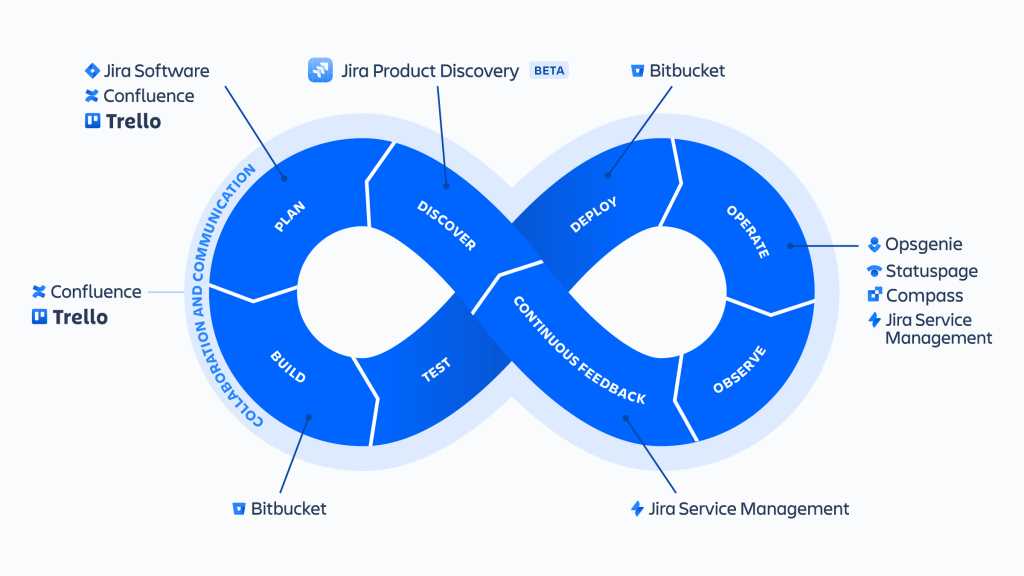
In today’s fast-paced IT landscape, streamlining operations is key to maintaining agility, efficiency, and quality. DevOps offers a range of best practices to help organizations enhance their IT operations. Below are some essential DevOps strategies to optimize your processes: 1. Embrace Continuous Integration and Continuous Delivery (CI/CD) Continuous Integration (CI) and Continuous Delivery (CD) form […]
Influencer Marketing 2.0 Building Authentic Collaborations

In today’s digital age, influencer marketing has evolved into one of the most powerful tools for brands to reach their target audiences. However, as the landscape becomes saturated, the focus has shifted from simply working with influencers to fostering authentic collaborations that resonate with consumers. In this blog, we’ll explore how Influencer Marketing 2.0 emphasizes […]
The Power of Personalization How to Create Data-Driven Marketing

In today’s highly competitive market, businesses must go beyond traditional marketing methods to stand out. One of the most effective ways to engage consumers and drive results is through personalization in marketing. By using data-driven marketing techniques, brands can create more relevant and personalized experiences for their customers. This not only increases engagement but also […]
AI-Powered Cybersecurity: The Future of Threat Detection

In an age where digital transformation is at the forefront of every industry, cybersecurity has become a paramount concern. With cyber threats evolving rapidly, traditional security measures often fall short. Enter AI-powered cybersecurity, a groundbreaking approach that leverages artificial intelligence to enhance threat detection and response. This blog explores the future of threat detection, the […]

